In recent years, data breaches and cyber attacks have become more frequent and sophisticated, causing significant financial losses to businesses of all sizes. As a result, the demand for cybersecurity professionals has skyrocketed, with companies eager to protect their sensitive information and prevent future attacks.
Toc
- 1. Introduction to EDR Cybersecurity
- 2. Benefits of EDR Solutions
- 3. Implementing EDR in Your Organization
- 4. Key Features of Effective EDR Solutions
- 5. Bài viết liên quan:
- 6. Comparison Edr with Other Cybersecurity Solutions
- 7. Future of EDR and Cybersecurity
- 8. Common Misconceptions About EDR
- 9. Conclusion
One type of cybersecurity tool that has gained popularity in recent years is Endpoint Detection and Response (EDR). This guide will provide IT professionals with an in-depth understanding of EDR and its role in enhancing an organization’s cybersecurity posture.
Introduction to EDR Cybersecurity

In the constantly evolving landscape of cybersecurity, Endpoint Detection and Response (EDR) has emerged as a critical component. With the increasing sophistication of cyber threats, traditional security measures are no longer sufficient. EDR offers advanced capabilities that make it indispensable in modern cybersecurity strategies.
What is EDR?
Endpoint Detection and Response (EDR) is a category of security tools designed to detect, investigate, and respond to cyber threats at the endpoint level. Endpoints are devices connected to a network, such as laptops, desktops, servers, and mobile devices. EDR tools work by continuously monitoring these endpoints for suspicious activity and flagging potential threats in real-time.
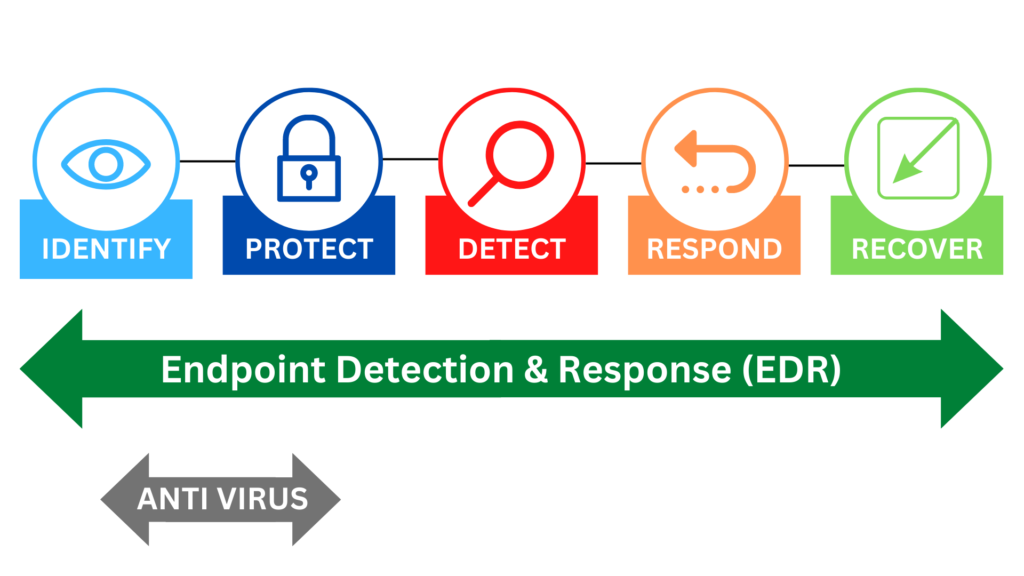
How does EDR differ from traditional antivirus software?
Traditional antivirus software works by scanning files or applications for known patterns of malicious code. In contrast, EDR uses behavioral analysis and machine learning algorithms to identify anomalies and patterns that may indicate an attack. This allows EDR to detect new or unknown threats that traditional antivirus may miss. Additionally, EDR provides detailed information on the detected threat, allowing for a more targeted and efficient response.
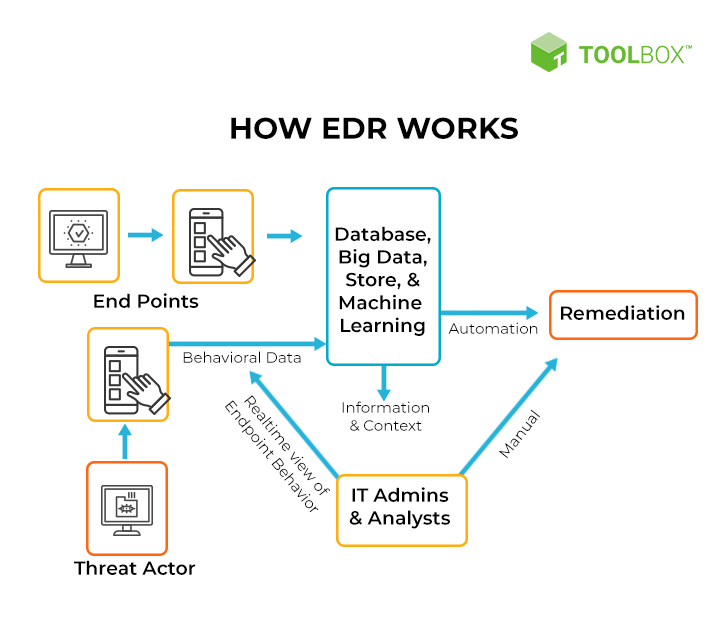
How Does EDR Work?
EDR solutions are designed to detect, investigate, and respond to suspicious activities on endpoints in real time. By continuously monitoring endpoint activities, EDR tools can identify unusual behavior and potential threats before they escalate. Once a threat is detected, EDR tools provide IT professionals with detailed information and analysis to help them understand the attack and take appropriate action.
Benefits of EDR Solutions
EDR solutions offer several benefits that make them an essential component of any modern cybersecurity strategy:
Real-time Threat Detection and Response
One of the most significant advantages of EDR is its ability to detect and respond to threats in real-time. Traditional security measures often rely on periodic scans, which can delay the identification of threats. In contrast, EDR solutions continuously monitor endpoint activities, allowing for immediate detection and response to potential threats.
Enhanced Visibility and Control
EDR tools provide IT professionals with detailed insights into endpoint activities, including user behavior and network traffic. This increased visibility allows IT teams to have a better understanding of their organization’s overall security posture and quickly identify any vulnerabilities or suspicious activities that may require attention.
Proactive Threat Hunting
In addition to real-time detection, EDR solutions also offer features for proactive threat hunting. This involves using advanced analytics and machine learning algorithms to search for potential threats proactively before they can cause harm. Proactive threat hunting can help organizations stay ahead of cyber threats and mitigate potential damages.
Implementing EDR in Your Organization
When considering implementing EDR in your organization, there are a few things to keep in mind:
Choose the Right EDR Solution
There are many EDR solutions available on the market, so it’s essential to choose one that best fits your organization’s needs. Consider factors such as budget, compatibility with existing security tools, and ease of use when evaluating different options.
Train Your IT Team
To effectively utilize an EDR solution, proper training is crucial. Make sure your IT team understands how to use the tool and its features correctly. Additionally, regular training and updates on new threats and techniques can help to maximize the effectiveness of EDR in your organization.
Integrate with Other Security Tools
EDR should not be seen as a replacement for other security measures but rather as an additional layer of defense. Integration with existing tools such as firewalls, antivirus, and SIEM solutions can bolster your overall cybersecurity posture.
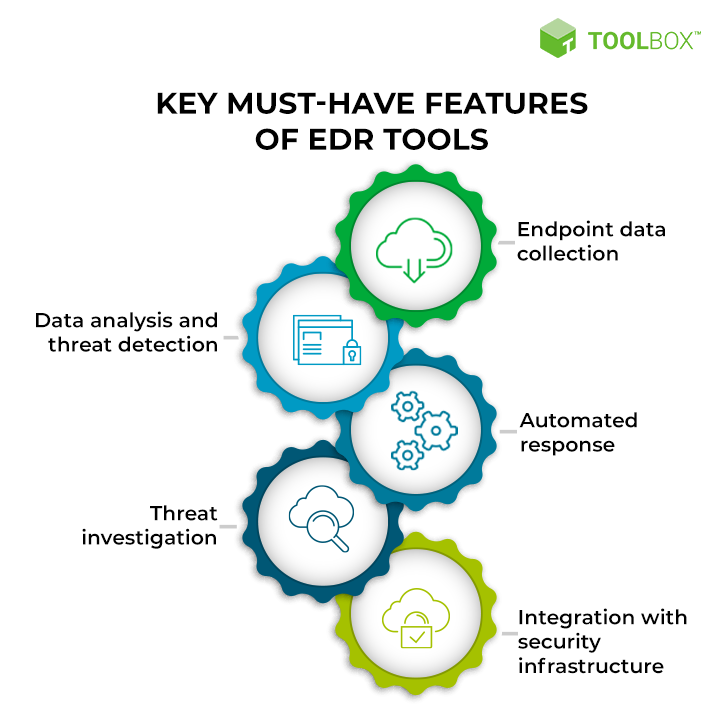
Key Features of Effective EDR Solutions
When evaluating different EDR solutions, here are some key features to consider:
Incident Response and Remediation
An effective EDR solution should not only detect threats but also facilitate swift response and remediation efforts. This includes capabilities such as automated threat containment, quarantine of affected devices, and the ability to roll back changes made by malware. These features help minimize the impact of a cyber attack and ensure that normal operations can resume quickly.
Behavioral Analysis
By leveraging behavioral analysis, EDR solutions can identify deviations from typical user or system behavior that may indicate a potential threat. This method allows for the detection of sophisticated and previously unknown threats that traditional signature-based detection systems might miss. Behavioral analysis helps in identifying malicious activities that could otherwise remain undetected.
Forensic Capabilities
Comprehensive forensic capabilities are essential for understanding the full scope of an attack. EDR tools often provide detailed logs and reports that help IT professionals reconstruct the events leading up to a security incident. This information is crucial for conducting thorough investigations and improving future security measures.
Scalability and Flexibility
As organizations grow, their cybersecurity needs evolve. An effective EDR solution should be able to scale with the organization, accommodating an increasing number of endpoints and adapting to changing threat landscapes. Flexibility in deployment options, such as on-premises, cloud-based, or hybrid solutions, can also be a significant advantage.
User-friendly Interface
A user-friendly interface can significantly enhance the efficiency and effectiveness of IT teams. An intuitive dashboard that presents critical information at a glance allows for quicker decision-making and more streamlined threat management processes.
Bài viết liên quan:
Expert Insights
“When evaluating EDR solutions, businesses should prioritize features such as machine learning for threat detection, automated response capabilities, and ease of integration with existing security infrastructure,” advises Rachel Lee, Director of Cybersecurity at SecureTech.
Comparison Edr with Other Cybersecurity Solutions

While EDR is a crucial component of modern cybersecurity strategies, it’s essential to understand how it differs from other security measures. Here are some key differences between EDR and other solutions:
EDR vs. Antivirus Software
While both EDR and antivirus software aim to protect against cyber threats, their approaches and capabilities are markedly different. Antivirus software primarily relies on signature-based detection to identify known malware and viruses. This traditional method involves scanning files and software against a database of known threats. However, antivirus software may struggle to detect new or sophisticated threats, as it depends on the regular updating of its threat database.
EDR vs. SIEM Solutions
Security Information and Event Management (SIEM) solutions focus on aggregating and analyzing security event data from multiple sources to provide a broad view of an organization’s security posture. SIEM systems excel at correlating data from various logs and generating comprehensive reports and alerts. However, unlike EDR, SIEM solutions do not typically offer the same level of real-time endpoint monitoring or threat remediation capabilities. EDR tools complement SIEM systems by providing granular visibility and direct response mechanisms at the endpoint level.
EDR vs. Firewalls
Firewalls are essential for protecting an organization’s network by controlling incoming and outgoing traffic based on predetermined security rules. They act as a barrier between secure internal networks and potentially harmful external networks. While firewalls are effective in preventing unauthorized access and blocking malicious traffic, they do not provide detailed insights into endpoint activities or offer advanced threat detection and response features like EDR solutions. Combining firewalls with EDR can create a more robust security framework.
Unique Capabilities of EDR
EDR solutions offer several unique capabilities that set them apart from other cybersecurity tools. One of the most notable features is their ability to provide comprehensive endpoint visibility. Unlike traditional security solutions, EDR tools continuously monitor and collect data from all endpoints, including desktops, laptops, and mobile devices, providing a holistic view of an organization’s endpoint security posture.
Another distinctive feature of EDR is its advanced threat-hunting capabilities. EDR solutions enable security teams to proactively search for threats within the network, often using advanced analytics and machine learning to identify hidden or emerging threats that could bypass conventional defenses. This proactive approach is critical in staying ahead of sophisticated cyber adversaries.
EDR platforms also excel in providing detailed forensic analysis and incident investigation. When a security incident occurs, EDR tools can recreate the attack timeline, offering insights into how the threat entered the network, what actions it took, and how it spread. This information is invaluable for understanding the attacker’s tactics, techniques, and procedures (TTPs) and for preventing future incidents.
Additionally, EDR solutions often include automated response capabilities. In the event of a detected threat, EDR tools can automatically take actions such as isolating affected endpoints, terminating malicious processes, and removing malware. This rapid response helps mitigate the impact of an attack, reducing downtime and the potential for widespread damage.
The Future of EDR
As cyber threats continue to evolve, EDR solutions are expected to become even more sophisticated. Future advancements may include enhanced integration with other security technologies, greater use of artificial intelligence and machine learning for threat detection, and improved automation for incident response. Organizations that invest in robust EDR capabilities will be better equipped to navigate the complex and ever-changing cybersecurity landscape.
Future of EDR and Cybersecurity
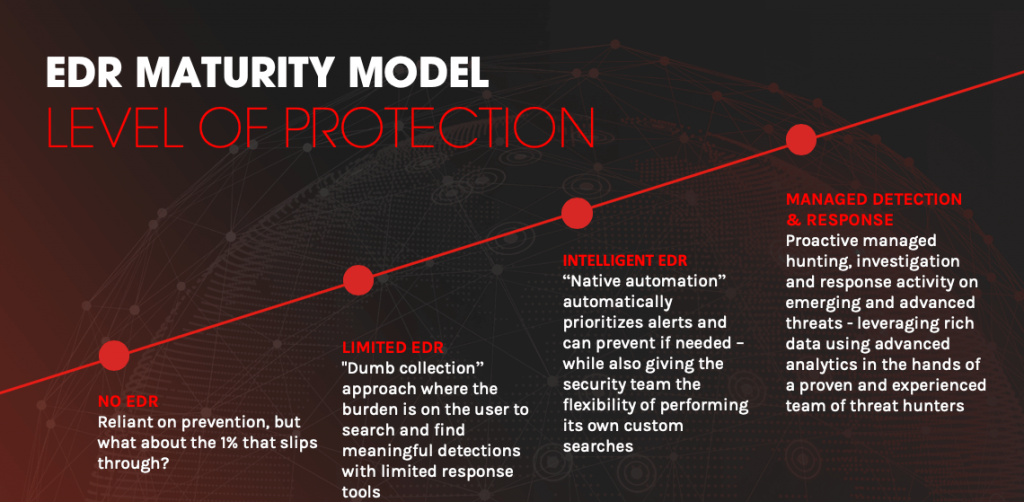
Importance of Continuous Monitoring and Updates
In the dynamic world of cybersecurity, continuous monitoring and regular updates are essential to maintaining an effective defense against emerging threats. EDR solutions are designed to evolve alongside the threat landscape, with frequent updates that incorporate the latest threat intelligence. This ensures that the system remains effective at detecting and responding to new types of malware, phishing attacks, and other cyber threats. Continuous monitoring also allows for the early detection of anomalies within the network, enabling prompt action to mitigate potential security incidents.
Training and Awareness
Equally important to the technology itself is the human element of cybersecurity. Training and awareness programs are crucial in ensuring that employees understand the role they play in maintaining the organization’s security posture. By educating staff on the importance of basic cybersecurity practices, such as recognizing phishing attempts and properly handling sensitive data, organizations can significantly reduce the risk of human error leading to security breaches. Effective EDR solutions often include features that help in training and raising awareness, such as automated alerts and educational pop-ups that inform users about potential threats and best practices.
Integration with Security Frameworks
For optimal results, EDR solutions should integrate seamlessly with an organization’s existing security frameworks and infrastructures. This includes compatibility with other cybersecurity tools like SIEM systems, firewalls, and identity management solutions. An integrated approach allows for the consolidation of various security functions, providing a more comprehensive defense mechanism. It also facilitates better communication and coordination between different security layers, enhancing overall incident response times and effectiveness.
Common Misconceptions About EDR
Despite the clear benefits of EDR solutions, there are several misconceptions that can prevent organizations from fully leveraging their capabilities. One common misconception is that EDR is only necessary for large enterprises with vast IT resources. In reality, organizations of all sizes can benefit from EDR, as small to medium-sized businesses are often targeted by cybercriminals due to perceived vulnerabilities.
Another misconception is that EDR solutions are overly complex and difficult to manage. While EDR technology can be sophisticated, many providers offer user-friendly interfaces and comprehensive support services to help organizations deploy and manage their solutions effectively. Moreover, the complexity is often outweighed by the advanced level of protection and visibility that EDR provides.
There is also a misunderstanding that deploying EDR eliminates the need for other security measures like antivirus software or firewalls. EDR is most effective when it complements existing security measures, enhancing the overall security posture of an organization by providing endpoint-specific insights and responses.
The final misconception is that EDR solutions are prohibitively expensive. While cost can be a concern, the potential savings from preventing a major security incident often justify the investment. Additionally, many providers offer scalable solutions to fit different budgets, ensuring that a wide range of organizations can enhance their endpoint security without breaking the bank.
By addressing these misconceptions, organizations can make more informed decisions and achieve a higher level of cybersecurity resilience with EDR solutions.
Conclusion
In conclusion, the rapidly evolving landscape of cyber threats necessitates the adoption of advanced security measures such as EDR solutions. These tools provide unparalleled visibility into endpoint activities, proactive threat hunting capabilities, detailed forensic analysis, and automated response mechanisms. By integrating EDR with other security solutions like SIEM systems and firewalls, organizations can build a comprehensive and resilient cybersecurity infrastructure.
Investing in continuous monitoring, regular updates, and employee training forms the backbone of an effective cybersecurity strategy. It ensures that the organization is well-prepared to detect and respond to emerging threats promptly. As technologies advance and cyber adversaries become more sophisticated, the role of EDR in safeguarding sensitive data and maintaining operational integrity will increasingly become paramount. Organizations that prioritize these measures will not only strengthen their security posture but also pave the way for a more secure digital future.












